The New Face of Resilience
When Europe’s Digital Operational Resilience Act (DORA) takes full effect in January 2025, it won’t just be another compliance milestone — it’s a turning point in how financial institutions define trust, continuity, and control.
For decades, operational risk focused on controls and audits. DORA shifts the conversation toward continuous resilience — the ability of banks, payment processors, and even cloud providers to withstand, recover, and learn from digital disruptions.
And in an age where AI systems, cloud infrastructure, and automation form the nervous system of financial operations, DORA forces a fundamental question:
“Can your technology recover faster than your customers lose trust?”
Why DORA Matters Now
DORA applies to virtually every entity in the financial ecosystem — from global banks to fintechs and ICT third-party providers (including cloud, SaaS, and AI service vendors).
Its mission is simple but sweeping:
“Ensure the entire financial sector can resist, respond to, and recover from ICT-related disruptions.”
Unlike older frameworks that focused on documentation, DORA mandates proof of operational resilience through testing, incident reporting, third-party oversight, and governance evidence.
In short: resilience isn’t a report anymore — it’s a capability.
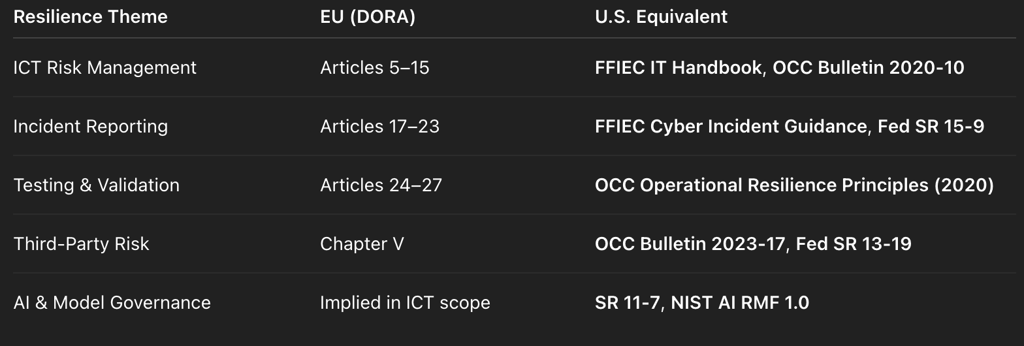
DORA’s Five Pillars of Digital Resilience
1. ICT Risk Management (Articles 5–15)
Firms must establish governance structures, board accountability, and controls that span all critical systems — including those leveraging AI/ML or cloud.
Key takeaway: resilience must be engineered, not audited.
2. Incident Reporting (Articles 17–23)
DORA introduces harmonized standards for classifying, tracking, and escalating ICT incidents within tight timelines — creating transparency across the financial ecosystem.
3. Digital Resilience Testing (Articles 24–27)
Beyond routine testing, DORA calls for Threat-Led Penetration Testing (TLPT) — simulating real-world attacks and failure scenarios.
In practice, this means testing AI models, APIs, and orchestration layers that may act autonomously in production environments.
4. Third-Party Risk Management (Chapter V)
Financial institutions must monitor the resilience of their critical technology service providers (TSPs) — including hyperscalers, AI model providers, and SaaS vendors.
DORA introduces a new role: “Lead Overseers” — regulatory authorities with direct audit access to TSPs.
5. Information Sharing & Collaboration (Chapter VI)
Encourages sector-wide intelligence exchange to strengthen collective defense against emerging threats — a model mirrored in U.S. cybersecurity coordination.
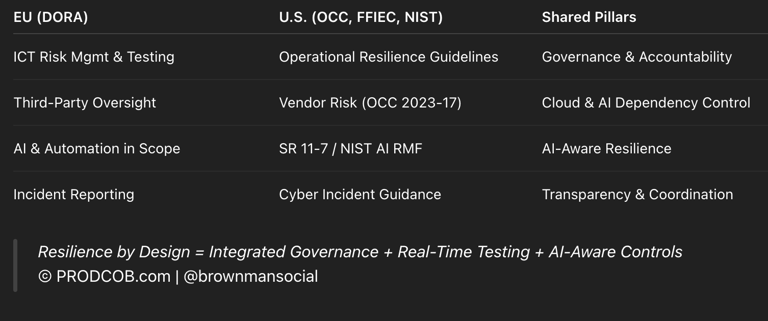
The U.S. Parallels: Converging Paths to the Same Goal
Though DORA is European, its core principles echo across the Atlantic.
Both regions are converging on the same thesis:
Resilience is the ultimate control.
Whether you’re governed by the European Banking Authority or the U.S. Federal Reserve, the expectation is identical — prove you can recover and continue operations without systemic impact.
AI, Automation, and the Resilience Challenge
Here’s the paradox: the very technologies improving speed and efficiency — AI, ML, cloud orchestration, and RPA — also amplify systemic dependencies.
Consider these scenarios:
A GenAI model introduces incorrect transaction routing logic.
An AI-powered fraud engine misclassifies thousands of accounts.
A cloud outage cripples a core risk-monitoring workflow.
Under DORA, these are not just operational events — they are ICT incidents with governance implications.
To align AI-driven systems with resilience principles, institutions must:
Extend resilience testing to include AI models, pipelines, and data drift.
Embed monitoring hooks in ML Ops pipelines for anomaly detection.
Link model inventories to ICT registers, ensuring traceability.
Simulate failure propagation across microservices and dependencies.
In essence, AI now sits inside the resilience perimeter.
Bridging Frameworks: DORA Meets NIST, FAIR, and ISO 42001
Each framework brings a complementary dimension to resilience:
NIST CSF 2.0 → Defines functions: Identify, Protect, Detect, Respond, Recover.
FAIR Risk Quantification → Converts resilience metrics into financial exposure.
ISO 42001 (AI Management System) → Ensures AI systems are governed and monitored consistently.
DORA → Enforces operational validation, incident traceability, and cross-entity oversight.
Together, they form a unified Resilience-by-Design architecture — one that is both measurable and auditable.
How to Operationalize Resilience by Design
1. Map Critical Business Services
Identify dependencies across human, process, and technology layers — especially those involving automation and AI.
2. Integrate Risk, Compliance, and Engineering Teams
Break silos. Resilience is achieved when model validators, engineers, and compliance officers share metrics, not memos.
3. Automate Evidence Collection
Use continuous monitoring, system logs, and API telemetry to create real-time regulatory evidence.
4. Test Continuously, Not Annually
Adopt “Resilience-as-Code” — embedding self-healing, fault injection, and chaos testing into CI/CD pipelines.
5. Strengthen Third-Party Assurance
Move beyond questionnaires — demand resilience metrics, AI transparency reports, and shared testing results from cloud and AI vendors.
Resilience by Design = Integrated Governance + Real-Time Testing + AI-Aware Controls